
How to Build Your No-Code KYC Workflow (and Ship It to Production Today)
Key takeaways (TL;DR)
A KYC workflow is the structure that defines how you verify identities, apply AML controls, and make automated decisions.
No-code workflows let you launch tailored verifications without depending on engineering.
Automating KYC reduces onboarding friction, boosts conversion, and can cut operating costs by up to 70%.
Didit offers a visual builder with document, biometrics, and screening modules—fully auditable and compliant with GDPR and AML/CFT.
If you lead a compliance or engineering team at a fintech or any platform with onboarding, you’ve heard this before: KYC never “ends.” Regulations change, fraud evolves, and teams need to roll out updates fast.
What happens when everything depends on engineering? Users drop off (as high as 63–67% in long or confusing digital flows, according to recent industry reports), costs spike, and customers are lost to onboarding delays.
In fact, 70% of banks say they’ve lost customers due to onboarding delays, per multiple studies.
Meanwhile, identity verification demand keeps growing—over 70 billion checks in 2024, per Juniper Research—and compliance teams are still battling massive false positives during AML screening.
A no-code KYC workflow tackles these pain points: it lets you design, publish, and audit the flow in minutes, reduce friction where it adds no value, and tighten controls without blocking product.
What a KYC Workflow Is (and Isn’t)
A KYC workflow is the orchestration of steps, rules, and decisions that end in approved, in review, or declined. Every company adapts its flow to its policies, but it typically combines data and document capture, biometrics (1:1 Face Match and Passive Liveness), and AML screening, plus age checks, proof of address, or risk questionnaires.
A KYC workflow isn’t just a pretty form or a rigid SDK—it’s governed business logic, with versioning and traceability, adjustable by risk, country, or product, without touching code.
On platforms like Didit, you build this flow visually with a no-code builder: pick modules (document, biometrics, screening, etc.), define rules, and publish to production in minutes—no engineering dependency.
Compliance Requirements (practical summary)
Beyond identity verification, financial institutions must meet Anti-Money Laundering and Counter-Terrorist Financing (AML/CFT) obligations.
A solid KYC flow includes:
- AML screening: checks against sanctions, watchlists, PEPs, and adverse media.
- Data minimization and retention aligned with GDPR.
- A clear, documented legal basis.
- Segmentation by geography and vertical (Spain vs. Brazil is different; so is a gym vs. an exchange).
With a no-code approach, this configuration lives in policy controls managed by the compliance team itself—freeing engineering to focus on core work.
No-Code Workflow Architecture
A no-code KYC workflow relies on three main layers:
- Visual orchestrator. A canvas to map steps, branches, timeouts, retries, and exception handling. In Didit, each block (document, biometrics, screening) is configured with clear parameters and connected—no code required.
- Plug-and-play connectors. Assemble the verification flow for your business needs: add, remove, or tune modules (OCR, AML, messaging, biometrics) without rebuilding the UX.
- Data & audit. Immutable logs for verification status, artifacts (selfies, PDFs, hashes), and role-based permissions to ensure segregation of duties.
Thanks to no-code workflows, you can change rules and ship new versions to production with full control and traceability.
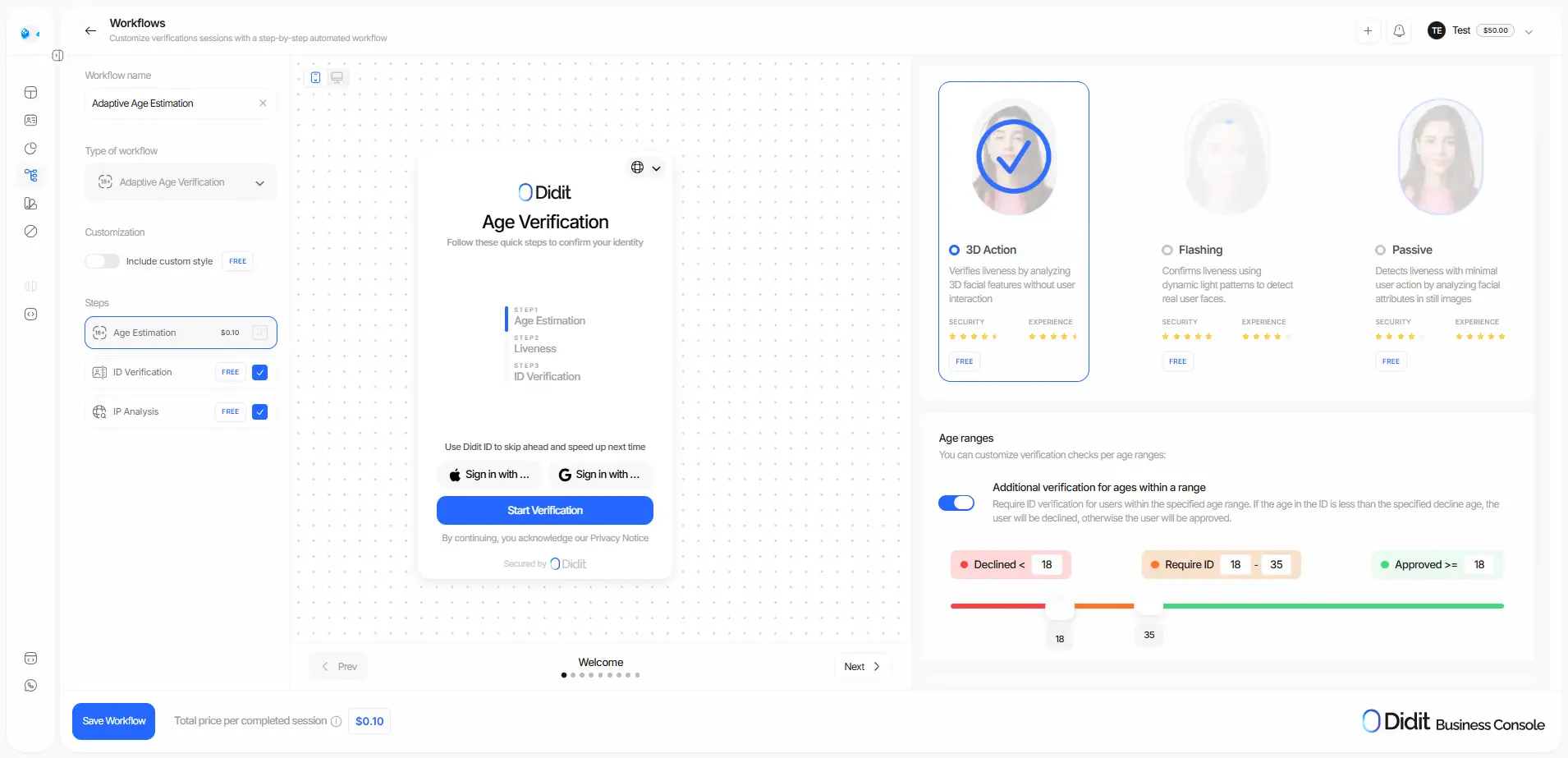
Designing the Journey: states, rules, and tolerances
Before using the visual orchestrator, define all verification states and when they apply: Not Started, In Progress, Approved, Declined, KYC Expired, In Review, Expired, or Abandoned.
On that foundation, set risk thresholds and gray zones: factor in biometric indicators, AML screening results, and automated rules to decide which sessions are approved, rejected, or routed to review.
Also add fallbacks for key features—e.g., in Age Estimation, request document verification if the biometric estimate falls into a gray zone.
A well-designed layer can recover a significant share of verifications and lift conversion.
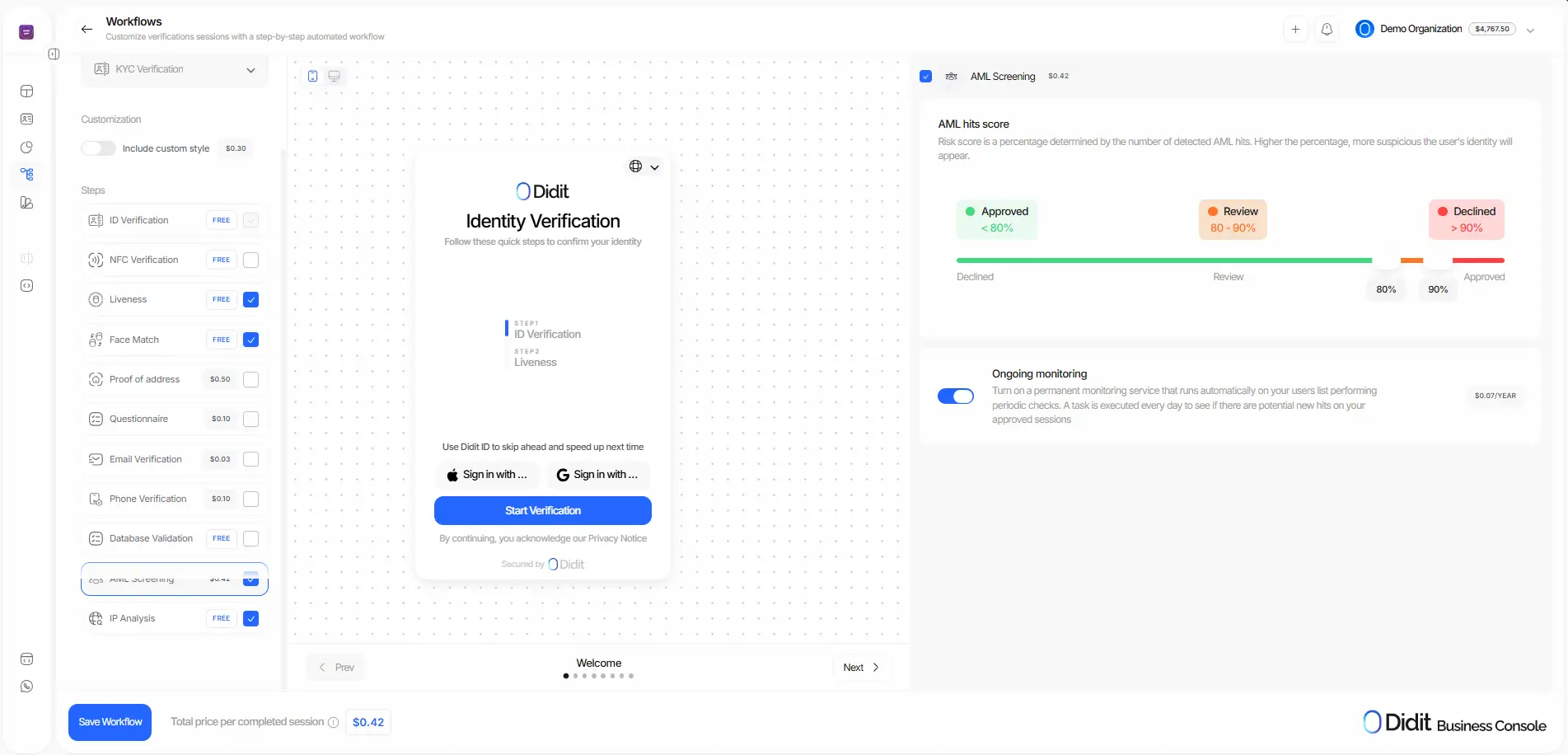
Screening and Risk Scoring
AML screening isn’t a binary “yes/no.” Fuzzy matching handles name variants, accents, and transliterations to widen detection.
You can also tune controls by jurisdiction, product, and customer risk, with databases that update continuously.
When false positives occur—as they often do—define auditable auto-clear criteria (e.g., name match but different date of birth) and allowlists for legitimate repeat matches.
Manual review and four-eyes (no code)
Most cases will resolve automatically, but some need manual review: broad thresholds, AML hits, document inconsistencies, or elevated risk.
Prioritize by risk, country, or reason, and apply the four-eyes principle (UNIDO) where appropriate: certain risk decisions must be validated by two separate people.
Everything should leave an auditable trail—logs are your best defense.
Exporting sessions should also be one-click for audits or internal reviews.
Operational automation (without engineering)
A strong KYC workflow builder lets you automate the entire process with zero code: document verification, biometric validation, AML screening, and automated decisions (approve, decline, review).
Operational automation lowers abandonment and prevents human error while preserving traceability. The key: everything is configured, not programmed.
Optimizing friction and cost
The goal isn’t to “pass everyone,” but to pass good users at the lowest possible cost. Activate modules by risk, country, or product—not every user needs the same depth of verification.
With modular solutions like Didit, you avoid rigid bundles and pay only for completed verifications.
The Free KYC plan (document verification, unlimited 1:1 Face Match and passive liveness) can reduce operating costs by up to 70%, based on real Didit customer cases.
By automating processes, reducing false positives, and optimizing module order, you increase conversion and lower CAC.
Friction-driven abandonment is real—and it can surge if verification is clunky—so controlling it is key to protecting revenue.
Conclusion
Building a no-code KYC workflow is the fastest, safest way to launch tailored verifications without overloading your engineering team.
It empowers compliance to govern policies, thresholds, and regulations; and engineering to iterate faster—reducing cost and time to market.
With Didit, you can do it today: build, version, audit, and scale your KYC workflow without compromising compliance or user experience.
How to Build Your No-Code KYC Workflow (and Ship It to Production Today)
